Authentication Authority
True to the name "AuthentX," all XTec products are designed to support strong authentication. After all, security, mutual authentication, and the unchallenged ability to rapidly process cryptographic authentication are what set XTec apart.
The Authentication Authority, a GSA FIPS 201 approved product, is central to the AuthentX end-to-end infrastructure because it enables it to validate authenticated transactions. As such, the Authentication Authority has built-in capabilities to act as an Online Certificate Status Protocol responder. But it is not just a standard OCSP; it is capable of all major protocols.
Enterprise Solution
Moreover, the Authentication Authority is an integral piece of an enterprise infrastructure, equipped with physical and logical provisioning, monitoring, alerts for suspicious activity, and instant, real-time status reporting for native credentials. The Authentication Authority is a bridge between your existing internal infrastructure and even external components, the Authentication Authority streamlines credential usage by leveraging your current investments and applying strong authentication and validation to your organization in its entirety.
4-in-1 Functionality
The Authentication Authority can be configured to perform validation duties in the three major protocols: CRL, LDAP, and OCSP. The Authentication Authority is RFC2560 compliant and capable of SCVP. It can serve as a temporary cache for visiting credentials while offering real-time status results for native credentials stored in the AuthentX IDMS/CMS. This capability enables instant revocation for both physical and logical transactions.
With other vendors, this functionality alone would require multiple products. But XTec’s Authentication Authority offers this and much more.
Monitoring
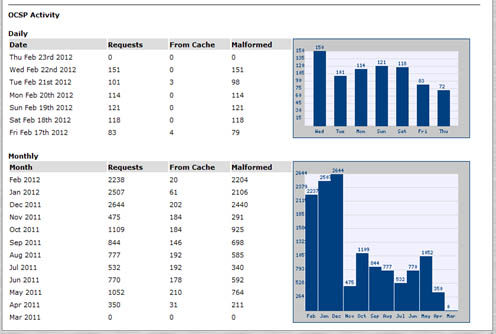
The Authentication Authority comes equipped with a web-based, live dashboard depicting your infrastructure’s transactions – both physical and logical. This feature, unparalleled by other vendors, offers C-Level executives easy access to usage data.
More importantly, the dashboard is valuable for monitoring the status of the responder as well as raising concerns when suspicious activity occurs. For example, if concurrent attempts at access are unsuccessful or if a single credential or digital identity attempts to access various applications from different locations, the dashboard can alert administrators.